While online shopping is much more convenient than navigating densely packed shopping centers, it also brings its own set of challenges. Cybercriminals exploit the increased online traffic and shoppers' eagerness for deals, intensifying their attacks with scams, phishing, and fraudulent offers to deceive unsuspecting buyers.
Veraciti Inc.
Blog
Copilot Pro vs. Microsoft 365 Copilot: Which AI assistant is right for you?

Copilot Pro and Microsoft 365 Copilot are two cutting-edge artificial intelligence (AI) assistants that are shaping the future of work by streamlining tasks and boosting productivity. In this blog post, we'll delve into their features, benefits, and limitations to help you choose the right AI assistant for your business's needs.
From legacy to cloud: Migration strategies you should follow

Outdated legacy applications can hold businesses back, hindering growth and innovation. But with the power of cloud technology, you can breathe new life into your aging software systems. Migrating legacy applications to the cloud not only addresses operational and security concerns but also unlocks a world of possibilities.
Why managed IT is the perfect holiday gift for your business
Retailers: Don’t let the Grinch steal your cheer (and your customer data)
Fortify your Android device and data with these new theft protection features
Say goodbye to sluggishness: Easy tricks to boost your iPhone’s performance
For many workers, iPhones are practical business tools — they make handling emails, presentations, and everything in between simple and easy. But these devices can become slow and unresponsive, which can disrupt your day and hinder productivity. By implementing the following five hacks, you can keep your phone running at its best and minimize sluggish performance.
How to resolve Windows issues with an in-place upgrade install
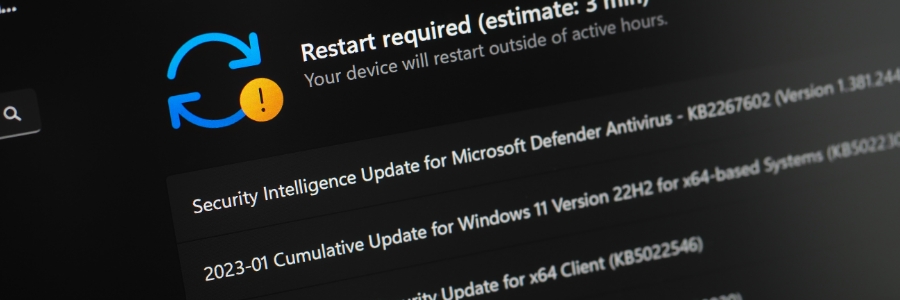
Is your Windows computer acting sluggish, displaying strange errors, or refusing to cooperate? Before resorting to a full reinstall, try installing a Windows in-place upgrade. This simple process can fix many common issues without wiping your data.
What is a Windows in-place upgrade install?
A Windows in-place upgrade refreshes your operating system without deleting your personal files, settings, or installed applications.
The power of Infrastructure as Code in scaling Internet of Things networks

The Internet of Things (IoT) has been key toward revolutionizing industries, connecting devices, and enabling data-driven insights. However, scaling IoT networks is becoming a challenge as the number of devices continues to increase. To address this, infrastructure-as-code (IaC) provides seamless scalability and efficient management of IoT infrastructure.





